Drive your attack surface with a single source of truth
Gather and unify your IT & Cyber data to quickly discover your inventory gaps, prioritize your remediation actions and accelerate your audits.

Your IT & Cyber teams waste 52%* of their time manually gathering data

With OverSOC,
focus on the essentials.
Collect data from all the tools used by your IT and SecOps teams (via API), as well as data from your business teams (via flat files), and bring them together in a single, agent-free database.
Don't waste time switching between 15 different tools.

Automate the ingestion, standardization and consolidation of your data in a common frame of reference. No more duplicate assets, no more copy-pasting into spreadsheets and manual dashboards!
Streamline the operations of your IT & SecOps teams, so they can concentrate where their expertise is needed.

Maximize your data enrichment by integrating external data sources such as security bulletins from certified sources.
Integrate business context with the Tag feature for decision-making aligned with your organization's strategic objectives.
Reduce risk by improving your vulnerability management and incident response.

Query your cyber data via the filter system and get accurate answers about the state of your information system.
Use OverSOC's pre-recorded filters, based on specific customer needs, or create your own filters and save them to share with your collaborators.
Quickly access key information and proactively monitor your information system.

Check the health of your information system and spot inconsistencies in the blink of an eye with our library of over 100 pre-configured KPIs, and set up alerts linked to these indicators.
Be warned of the risks before they become critical.

Generate tickets directly from OverSOC into your ticketing tool to orchestrate and delegate your remediation actions.
Facilitate the coordination of IT & SecOps teams.

Export your query results to remediation teams, share your associated filters and communicate the status of your information system more clearly to your staff thanks to a fast and easy data export.
Present cyber risks clearly and effectively.

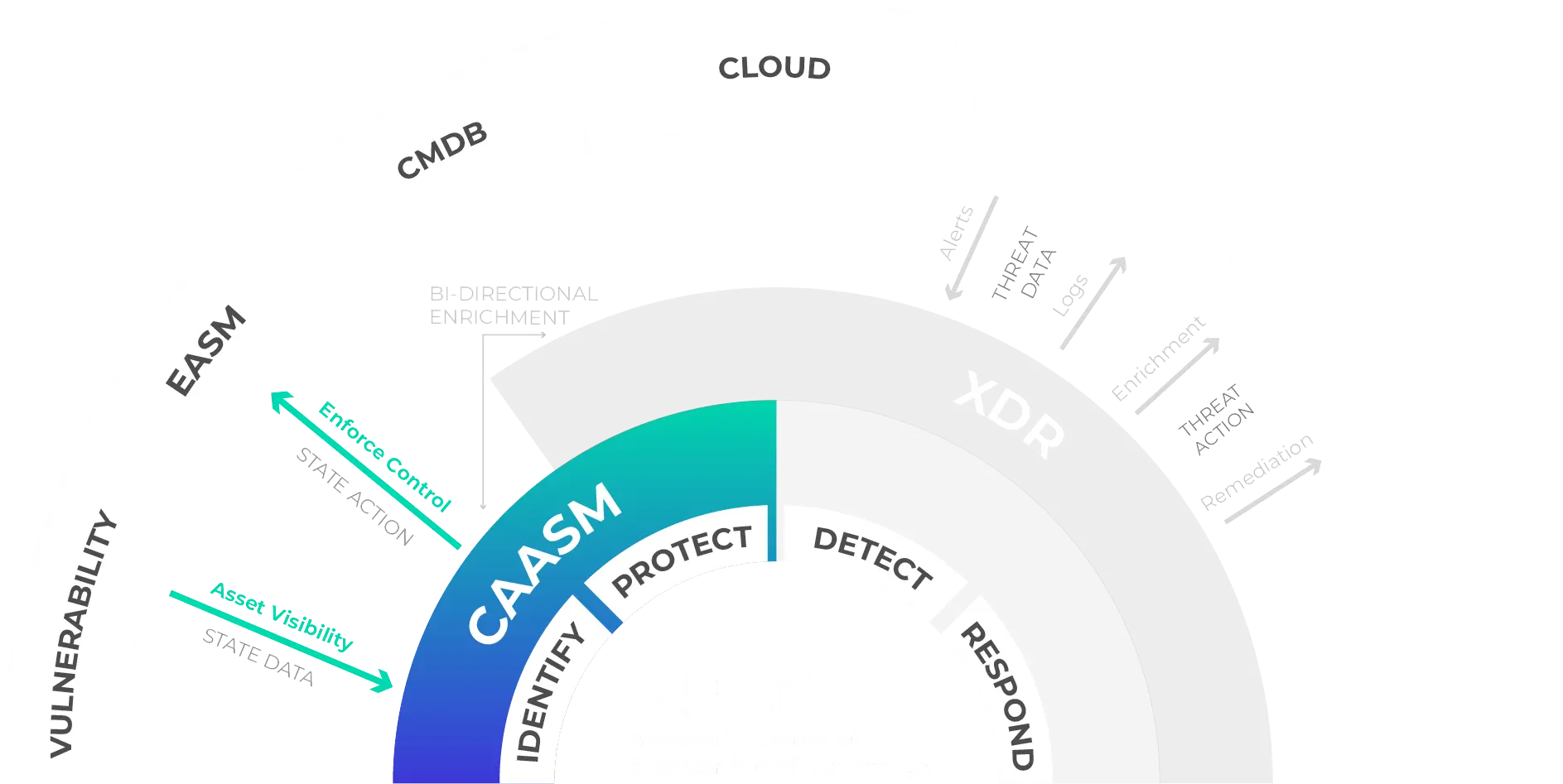
CAASM made in France
According to Gartner, Cyber Asset Attack Surface Management (CAASM) is a fast-growing solution that enables IT & Cyber teams to make the most of their existing asset management tools and data (hardware, applications, cloud and users). A CAASM solution collects existing data on assets (internal and external) from the various tools in place (CMDB, vulnerability scanning, etc.) via APIs or other imports, consolidates them and unifies them. This truth base is regularly updated via APIs, enriched by the business challenges of the various assets.
This regular consolidation enables inventory discrepancies to be identified very quickly, remediation actions to be prioritized easily, compliance audits to be prepared with peace of mind, and an operational, shared repository in the event of an attack.



Our second white paper written in partnership with CESIN
In 2023, we conducted a survey of CESIN CISOs to understand the level of cybersecurity maturity of French organizations, and their expectations of CAASM technology. We are delighted to be working with CESIN again this year to repeat this survey. Pre-register to receive this exclusive white paper as soon as it is available.
OverSOC wins the
"Military Cyber Operations Center" award

During the "Military Cyber Operations Control Center 3.0" challenge, we collaborated with Thales to revolutionize the visualization of cyberspace, with the aim of offering a view that is suitable for several profiles:
- Cybersecurity experts who want to facilitate their technical analyses
- Cyber command to support decision-making and the conduct of operations
- High-level authorities for understanding operational status updates




A team located on the Campus Cyber Hauts-De-France

As a local player rooted in the Hauts-de-France region's cyber ecosystem, OverSOC is in a privileged position to understand the specific challenges facing companies in the region, helping them to implement effective preventive measures to protect their assets and strengthen their security posture, agility and resilience.
.webp)

















.webp)
























